Authorization flow with PKCE in the terminal
Written by Bjørn Einar Bjartnes
Authorization flow with PKCE is one example where it is hard to use the terminal and tools such as CURL only. We quickly get into an integration to a full-fledged web application using code-on-demand and other fanciness from the web that is hard to consume using our basic command line tools.
In this blogpost I will show how to spin up the browser and get its callbacks, which helps us understanding the integration points between our web application and the identity service (In this case, Azure B2C).
This I think I need to write a blog post to explain, but the idea is that we can use the terminal and plain HTTP also when we want to trigger and get flows back from more advanced hypermedia dances such as login-flows (this case Authorization flow with PKCE to Azure B2C). pic.twitter.com/6i6lk4ocMP
— B.E. Bjartnes (@bjartnes) June 6, 2022
The code challenge and verifier can easily be ignored in understanding the principles, they are a security mechanism described in RFC 7637.
We begin by invoking the web application by a GET with some query parameters. For this demonstration, the most imporant detail is the redirect URL, in this case http://localhost:8888. The contract is described in detail here. When we fire up the browser and start the login flow, a lot of things is happening that are outside our control. The main think to notice, is that nothing of this is part of our application, we do not have to do anything until the flow redirects the browser to localhost:8888 again.
We use netcat to listen on port 8888, and a few commands to strip away everything coming back except the token.
When we get the response and the authorization token, we can post that to get id, bearer and refresh tokens back from the server.
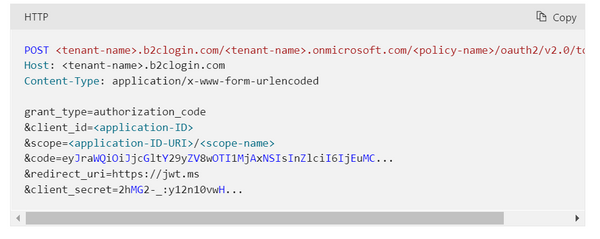
I find these exercices useful to be sure I have fully grasped how the integration works. In practice, one typically use a library on the client side to handle this. While this is simple and secure, it is not always very transparent and it can make it difficult to understand what is going on.